Ode to DYOR
One of the most important revolutions brought with blockchain and cryptocurrencies is ownership and banking freedom. But with great power comes great responsibilities. This new era comes with education, the new paradigm shift; not knowing and relying totally on third parties means losing security and ownership and is not the goal of these new technologies.
The internet was quickly successful because the mass adopters didn’t know what they were dealing with. They didn’t have to learn TCP-IP protocols to use it. But blockchain and cryptos is slightly different. Of course, you don’t have to learn how to code a smart contract or a blockchain protocol to use it, but some things are more important than others with everything you have to know:
- What is a private key and why it’s important;
- How to Do Your Own Research (DYOR) to not get scammed.
We recommend you read the Horizen Academy article about private keys, which will bring you lots of information about blockchain and crypto technologies, new articles are added often, so feel free to bookmark them and come back!
If you are here to learn about how to do your research and some tips to not get scammed, this article is for you. Note that new scam attack vectors can appear and that this list is not exhaustive.
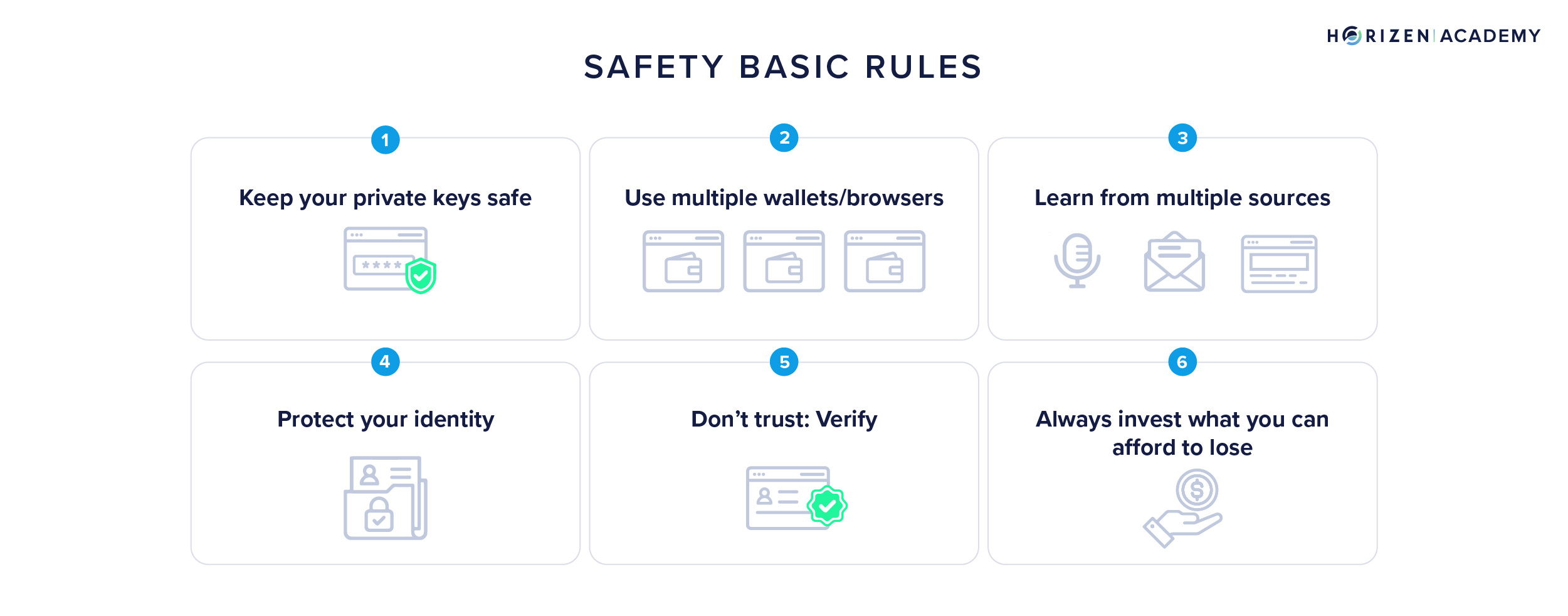
Basic Security Rules
These basic rules to protect yourself can apply to all Web 1 to Web 3 and would still be available up to Web 10.
- Don’t trust anyone; always verify the info yourself. Check the official sources for built-in applications, software, wallets, dapps, or smart contracts;
- Protecting yourself means protecting your online identity. We recommend you look at this article on the Horizen Academy to learn more about protecting your digital privacy (2FA, browsers, virtual phone numbers, etc.);
- Use multiple MetaMask/web wallet accounts connected to your browsers. If you want to participate in airdrops/tests, do it from a wallet with few cryptocurrencies. You can use them on different browsers and even different computers. One browser/computer will be reserved for more serious activities and the other for testing. It is the same as credit card payments on the Internet, for these purchases, it is recommended to use single-use cards, available in many neo-banks;
- Keep your private keys in a safe place, do not copy/save them on your computer, and never share them with anyone;
- Learn. You invest in cryptocurrencies and support some projects; you must know what you deal with. The Horizen Academy is a great tool to develop your knowledge, and it’s free! So use it as much as you need, get curious, and stay updated.
- Multiply the learning/media sources. If you see news somewhere, check on a second article that deals with the same information.
- Last but not least: with investments, always invest what you can afford to lose: even an audited project (even big audit companies!) can have non-spotted loopholes in its code.
Common scams
Scams existed long before blockchain, crypto, and DeFi. They even existed before the Internet! As technologies evolve, scams evolve too. But often, they use the same old designs. Let’s begin with basic scams.
Social Engineering
In Social Engineering, the scammer manipulates the user or a third party between him and the user (e.g. ISP, mailing services, telephone company, etc.) to get some vital information.
The user, or the third-party owning information on the user, thinks they are in a relationship with a trusted person and provides sensitive data. The relationship can last many days before the malicious actor gets access to this data.
Examples: The fake support center is a very common impersonator scam in crypto. Scammers talk in DM on social media to people seeking support to steal their personal information.
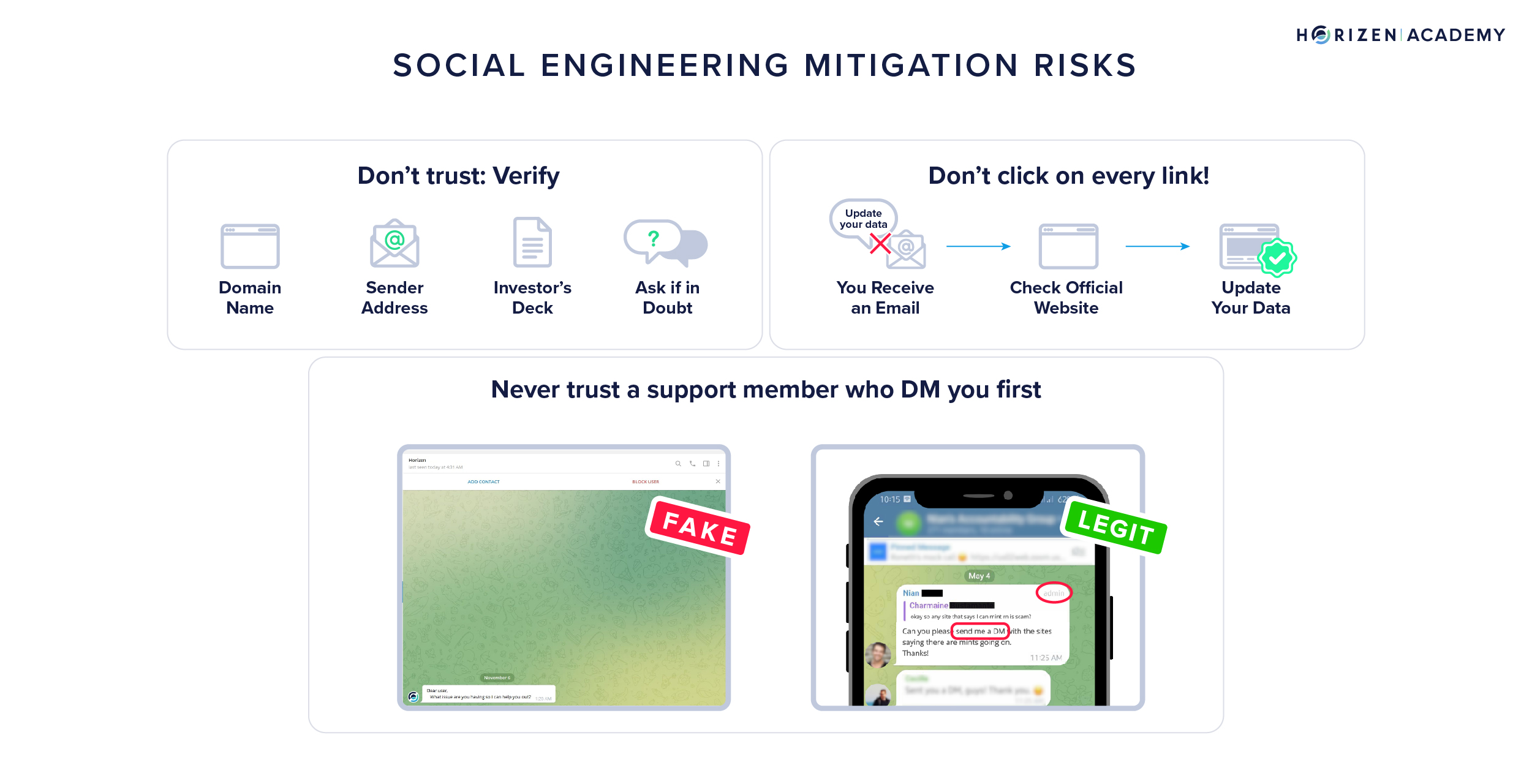
How to protect yourself from social engineering?
- Don't trust anyone;
- If you receive an email/call asking you to update your data, go to the website in question from your browser, not the links in the email. If you have data to update, you will be notified on your account on the website in question;
- Check the sender's email address carefully. If the brand name is misspelled or redirected after numbers and letters; it’s a fake one;
- Always look at the website address to be sure that you are on a good website: look for typos, https://, and extended domain names;
- A support service will never DM you first. If someone comes to help you in DM, it’s a 99% chance it’s a scam;
- Always check the links from official sources, such as the website or investor’s decks;
- In doubt, ask the support service on the official website/ social media.
Honey pots
A honey pot consists of making you think that you absolutely should invest in a project. They promise big incentives or have beautiful marketing.
That’s simple: if someone tells you to invest in a crypto that offers guaranteed returns, or huge and fast ROI, there are big chances that it is a scam.
Usually, the assets sent to the platform will be irretrievable.
Example: Evolved Apes
How to protect yourself from honey pots?
- Remember this motto: "If it sounds too good to be true, then it probably is."
- When there is a lot of marketing made and still no MVP
- Read the white paper: how in-depth is it?
Scams in DeFi
DeFi and liquidity pool rug pulls
Rug pulls consist of withdrawing all the funds users place on a project that looks promising, often through a backdoor written in the code.
Example: SQUID token, Luna.
About liquidity pool rug pulls, the scammer uses new DeFi products with new coins to make the user invest and steal his money.
*In a liquidity pool, users make cryptocurrencies available, on a pair at a time, for other users to borrow, lend, or trade via the pool. Exchanges are facilitated by moving from an order book technology, where a buyer must necessarily have a seller in front of him, to an AMM, Automated Market Maker, where the seller or buyer is no longer required in front of him to conclude the exchange.
In these rug pulls, users are incentivized to provide liquidity on a pair, for which they usually have to exchange (here, we say “swap”) BTC for the newly created token. To conclude the scam, the malicious actors remove all BTC from the pool.
How to protect yourself from a rug pull?
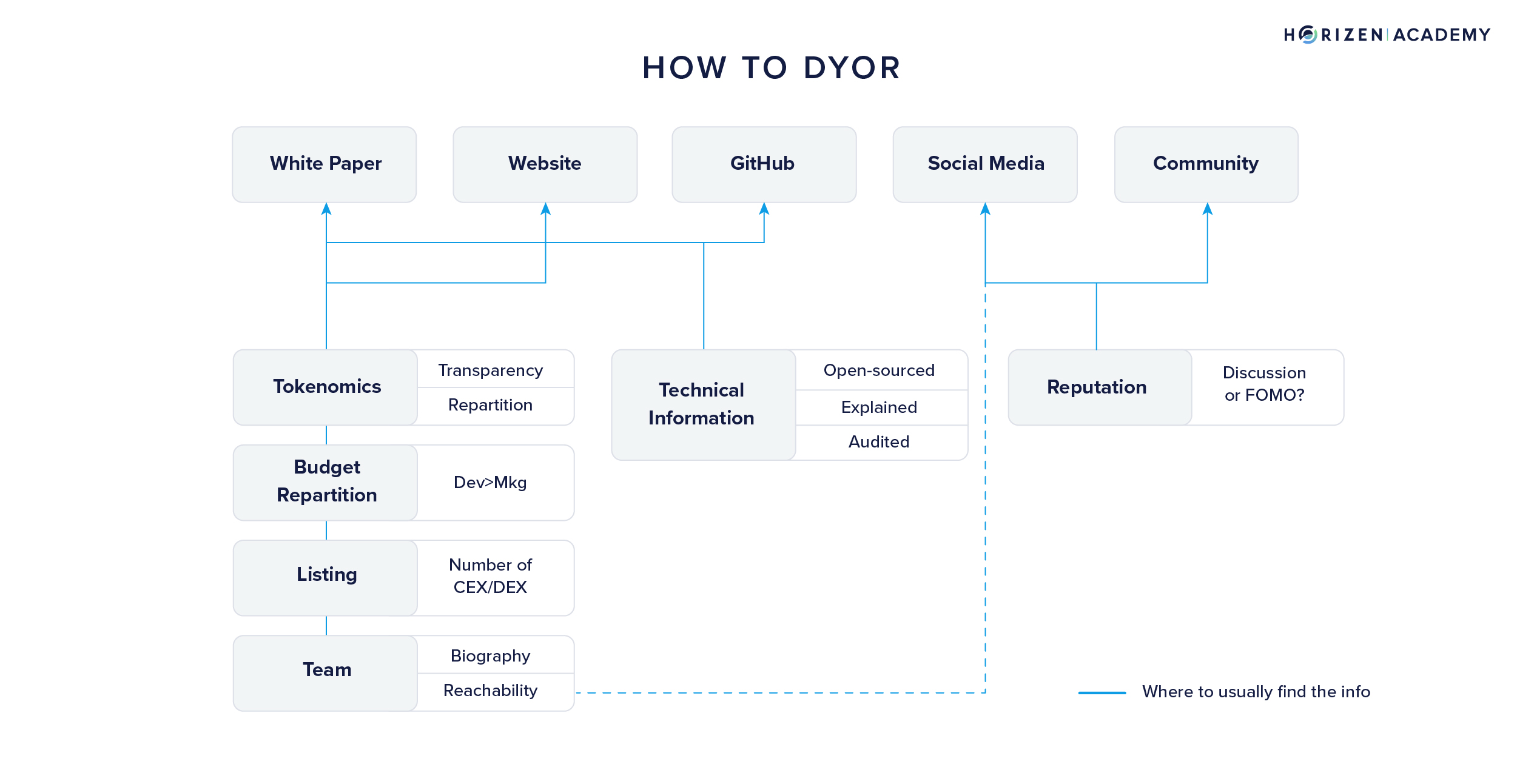
- DYOR: read the white paper, have a look at the team (can you find the information online and not only on the website?), verify the tokenomics and token projections, number of token holders, number of DEX used to list the token, verify if the code is open-source, audited, where is the development of the product compared to the marketing made.
- Hear the communities: go on social media, and talk to developers and other community members to know what they think about the project
Airdrop scams
The fake giveaway or airdrop scam consists of promoting a project/registering on a website in exchange for free cryptocurrencies or NFTs. When you try to retrieve the prize via a link, the malicious actor takes this opportunity to copy your account details and access your cryptocurrencies or NFTs. Another type of airdrop scam is to ask you to send some cryptocurrencies to receive more. A common example is the Elon scam, where a fake Elon Musk asks you to send some bitcoins, and they will send you twice as much!
How to protect yourself from Airdrop scams?
- Again, the answer will be: DYOR;
- Never send cryptos in the hope of receiving more;
- Make sure that the airdrop is made from an official account (check the website domain name, Twitter handle, etc.);
- Don’t access a website that sends a transaction to your wallet;
- Avoid high reward airdrops: it still can be legit if it’s high, but most of the time (99%), it won’t;
- Use a specific wallet to access these airdrops;
- Never participate in an airdrop sent via DM.

Pump and Dumps
Pump and dumps are common and well-known thanks to meme tokens. The marketing around the token will be focused on creating a FOMO (fear of missing out) to buy the token, and when the price is high, having the team sell their tokens to make a large profit. Note that it can happen in the crypto world and is not limited to DeFi protocols.
How to protect yourself from pumps and dumps?
- What is the token based on? Is the team easy to reach? Is the community speaking seriously and not just inviting you to FOMO?
- Read the white paper, and look at the website: if there is no product or service behind the token and it’s just a meme coin, be careful.
Wallet dusting
This scam targets hot wallets such as MetaMask by sending a transaction with a coin that will be used to track the other coins in your wallet. Usually, in hot wallets, you have the same address for every coin; the attacker can go to your wallet to look at your complete wallet and know exactly how many coins you hold there. Then he will try some phishing attacks to rob them from you. That can also happen when you download malicious software or crack, even outside the crypto world: they can have trojans or access your browser to steal your passwords and, possibly even, your funds.
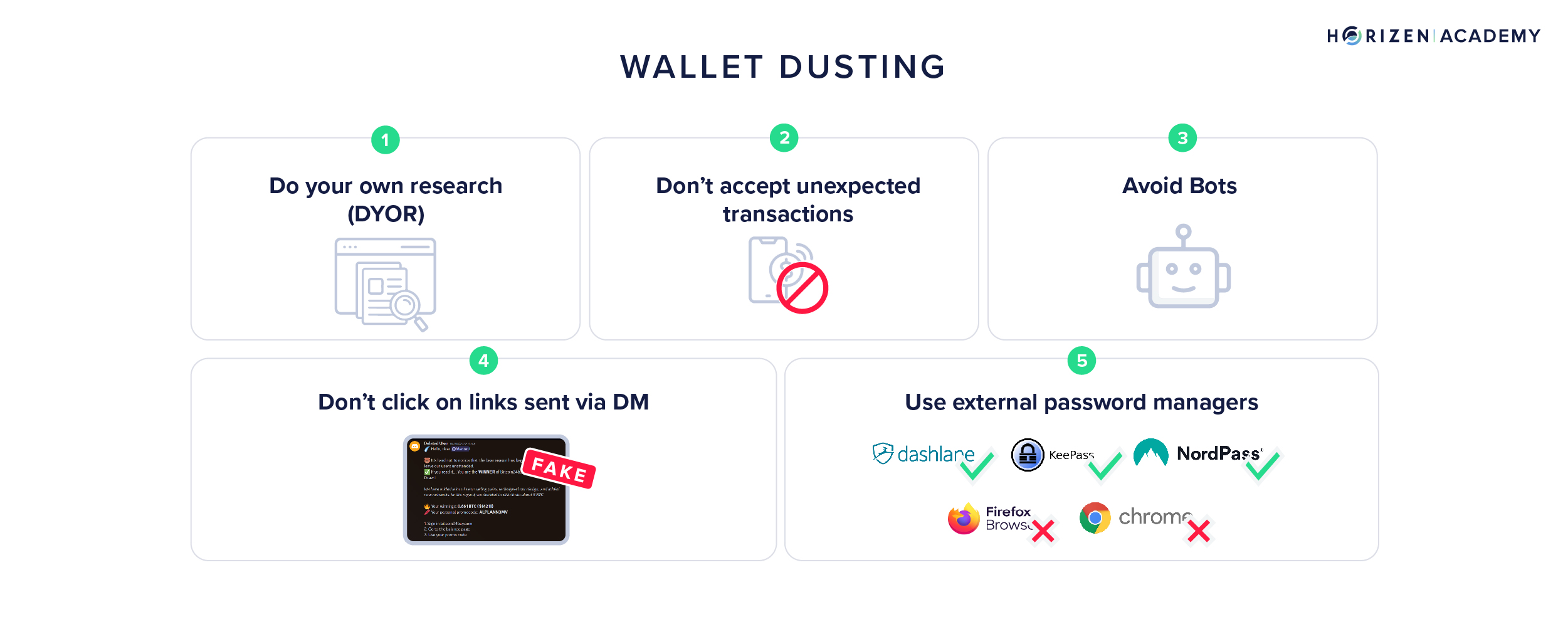
How to protect yourself from dusting?
- Never perform a transaction on a not well-known coin (DYOR first);
- Never accept transactions on your wallet if you don’t know where it comes from;
- Don’t click on links sent via DM from people you don’t know;
- Never use the browser to save your passwords, and if you are using an external tool, always use a master password;
- Don’t trust the bots mentioning MetaMask, Trust Wallet, etc.: They can send a command to steal your private keys.
Example: Bitctoin and Litecoin wallets dusting attacks
Point on Flash Loan Attacks
Flash Loan is not a scam, but it can offer the possibility. Albert Dessaint gives the best definition of Flash Loan: "This feat is made possible by the way this loan is structured: the borrower must contract, use and repay the money in a single transaction on the blockchain [...] By this structure, the counterparty risk is null because the money will be lent only in the case where the three actions are performed in a certain way".
For example, they are used to arbitrage (take advantage of a price difference between two exchange platforms) or swap the token several times during the buying/selling process.
The Flash Loan can allow some hackers to exploit its flaws. To do this, the attacker usually plays with several cryptocurrencies with low liquidity to artificially inflate the price and thus make gains.
How to protect yourself from flash loan attacks?
- Make sure the dex is audited;
- You can look at their bug bounty programs to see if a flaw was discovered;
- As with any investment: put only what you can afford to lose into the pools;
- Don’t invest a lot on low volume coins.
Example: Balancer Hack
Focus on NFTs
Non-Fungible Tokens are quite new in the Web3 ecosystem, and it’s easier to get scammed by something new, shiny, and in the grip of scams. NFTs, like other products, can be included in rug pulls, phishing attacks, pump and dumps. Some scams are more common in the NFT world than in the common crypto space.
Bidding scams
Bidding scams happen when you try to sell your NFTs on the secondary market. The malicious actor bids on your NFT but changes the cryptocurrency used without your knowledge, and you end up selling your NFT for way less than you were expecting.
How to avoid bidding scams?
Always look at the cryptocurrency used and don’t accept an offer if this one doesn’t fill your needs.
Counterfeit NFTs
Some scammers steal other NFT artists' creations. When you want to sell the NFT, the price may drop a lot if it’s noticed
How to avoid plagiarized NFTs?
Make sure you are buying from a trusted seller. Get your links from official sources.
Other scammy schemes
Invitations via DM
Invitations in DM to participate in a pump. Even if the person who comes in DM tells you they are honest, 99% aren’t. The best answer is to report them and block them.

To avoid this kind of scammy DMs, protect yourself on social media by disabling the possibility of sending you DMs.

Paid Google Ads Phishing
Google Ad scam is a type of fraud that involves creating fake ads on Google's advertising platform, Google Ads. These scams include creating fake websites or businesses that appear legitimate but are designed to steal account credentials or other important information.
How to avoid Google Ad scam?
- Use a browser that hides the Google Ad from Google search results;
- Check URLs for look-alike and typosquatting sites. Verify that it's the brand's legitimate domain.
- The domain in the ad may look correct, but once you open it, you may be redirected to a lookalike domain. - Double-check the domain once you are on the site.
- Do not use Google Ad links within search results; only click on actual search results.
Example with Trezor:

The URLs above obviously do not lead to the official Trezor website, but these scams can be harder to detect. For example, they may use domains like "biṇaṇce.com". You may not have noticed this initially, but it uses an "ṇ", a Latin character, instead of an "n".
Conclusion
The internet would be a safer place today with way fewer people scammed if education followed the mass adoption. We have to learn from our experiences, and these experiences lead us to make sure that the end-user understands what he deals with when he enters the crypto world to ride it safely. We hope this guide helped you to understand more about the risks in the digital age and made you want to continue learning more on this subject.